Process Detail
What is tpnumlkd.exe ?
tpnumlkd.exe is known as On screen display, it also has the following name On Screen Display or and it is developed by Lenovo Group Limited , it is also developed by Unknown. We have seen about 100 different instances of tpnumlkd.exe in different location. So far we haven't seen any alert about this product. If you think there is a virus or malware with this product, please submit your feedback at the bottom.Something wrong with tpnumlkd.exe ?
Is tpnumlkd.exe using too much CPU or memory ? It's probably your file has been infected with a virus. Let try the program named DriverIdentifier to see if it helps.How to remove tpnumlkd.exe
If you encounter difficulties with tpnumlkd.exe , you can uninstall the associated program (Start > Control Panel > Add/Remove programsWhat can you do to fix tpnumlkd.exe ?
Let try to run a system scan with Speed Up My PC to see any error, then you can do some other troubleshooting steps.If you think this is a driver issue, please try DriverDouble.com
Where do we see tpnumlkd.exe ?
Here is the list of instances that we see for the process: tpnumlkd.exe| Path | Product Name | Vendor | Version | Size | MD5 | |
| 1 | C:\Program\Lenovo\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.32 | 13830 | E982624511223F6605B815F7725FE8F8 |
| 2 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.73 | 18836 | A5A855EACC7AF263D5BC32D70CB6ABA0 |
| 3 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.33 | 16752 | C8B4599F87B8FE23AB4ACD3871CE9C5C |
| 4 | C:\Program Files\Lenovo\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.32 | 13830 | E982624511223F6605B815F7725FE8F8 |
| 5 | D:\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.35 | 16748 | 2B6A7F3D700545546C70D1DCD83BA464 |
| 6 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.35 | 16748 | 2B6A7F3D700545546C70D1DCD83BA464 |
| 7 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.40 | 18687 | 2BE2E4AD74B807691A3E8D2A6718BADB |
| 8 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.75 | 18807 | 0CF6D660AB3F85DB4C5F4846C37E6D01 |
| 9 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.46 | 18687 | EE67E9ED106D7CD0FBF35752E9852D81 |
| 10 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.33.1 | 9537 | 89D8C231936AB4EEAF995D642F3ADD3D |
| 11 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.47 | 18687 | 241A4865C177B56B4A6ED0F306CC0F8A |
| 12 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.50 | 18692 | 77DBBE46195AC705CE4C18E239094BD8 |
| 13 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.52 | 18641 | CCE4B2A3F02C3F61A60DFF7457790731 |
| 14 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.53 | 21252 | 6788DA20F2007E0E84E5749EE1CE2C49 |
| 15 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.34.0 | 9425 | 9BB2ABA91D3F9A55DDDCF929703C7F0E |
| 16 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.53 | 21252 | 587EB6B7EFD1A2CD1B4589602340F8F2 |
| 17 | D:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.50 | 18692 | 1765C22E1C77FE5AC591B8719FA3AB13 |
| 18 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.55 | 21293 | 5D056B64A4E67B16F3E606A52E4EC8C0 |
| 19 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.46 | 18687 | BEE22CDD96A72058D823FE58C8D7FE29 |
| 20 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.55 | 21293 | 1E72194F99E9C7C0AFA9485C51AA5DD0 |
| 21 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.50 | 18692 | 1765C22E1C77FE5AC591B8719FA3AB13 |
| 22 | C:\Program Files\Lenovo\HOTKEY\tpnumlkd.exe | On screen display | Lenovo Group Limited | 1.00 | 5260 | 17DD73B0BBBB722B9BCBDD5F15223BB1 |
| 23 | C:\Program Files\Lenovo\HOTKEY\tpnumlkd.exe | On screen display | Lenovo Group Limited | 1.22 | 13552 | 4B65B2918E301026CC4D40A9E47290B0 |
| 24 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.74 | 18933 | BA4FED0758BF2BBF52B0625FBC386B80 |
| 25 | c:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.71 | 18836 | CA06CE34D3FAC528F74A933F19933A4E |
| 26 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.51 | 18692 | 8FED703ED8E07230C5B427773C6D321F |
| 27 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.72 | 18938 | 0D1088C6DEFAE5F28AE1DE092AA3B392 |
| 28 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.71 | 18938 | 1562C429643F6995DE295AF3FF996851 |
| 29 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.45 | 18687 | 9B125F72268189CFB955E76D88C3D449 |
| 30 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.72 | 18836 | 8DAF9E74A04BB38722C59E2081C407EB |
| 31 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.74 | 18704 | 055292FE751DFD07781ED4E04246E5D4 |
| 32 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.52 | 18641 | C8A5EC440C16939EBC8CE4E1030EA5AF |
| 33 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.53 | 21252 | 6788DA20F2007E0E84E5749EE1CE2C49 |
| 34 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.33.1 | 9537 | 89D8C231936AB4EEAF995D642F3ADD3D |
| 35 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.74 | 18704 | 055292FE751DFD07781ED4E04246E5D4 |
| 36 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.73 | 18836 | A5A855EACC7AF263D5BC32D70CB6ABA0 |
| 37 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.34.0 | 9425 | 9BB2ABA91D3F9A55DDDCF929703C7F0E |
| 38 | C:\PROGRA~1\Lenovo\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.32 | 13830 | E982624511223F6605B815F7725FE8F8 |
| 39 | C:\PROGRA~1\Lenovo\HOTKEY\tpnumlkd.exe | On screen display | Lenovo Group Limited | 1.10 | 7827 | 74E50BDF1CD41A4FEDB89B9E2486EFCB |
| 40 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.55 | 21293 | 1E72194F99E9C7C0AFA9485C51AA5DD0 |
| 41 | C:\PROGRA~1\Lenovo\HOTKEY\tpnumlkd.exe | On screen display | Lenovo Group Limited | 1.00 | 5260 | 17DD73B0BBBB722B9BCBDD5F15223BB1 |
| 42 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.72 | 18836 | 8DAF9E74A04BB38722C59E2081C407EB |
| 43 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.33 | 16752 | C8B4599F87B8FE23AB4ACD3871CE9C5C |
| 44 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.51 | 18692 | 80658B6D9DFA9C7FCD0E0F2B97037148 |
| 45 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.71 | 18836 | CA06CE34D3FAC528F74A933F19933A4E |
| 46 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.46 | 18687 | EE67E9ED106D7CD0FBF35752E9852D81 |
| 47 | C:\PROGRA~1\Lenovo\HOTKEY\tpnumlkd.exe | On screen display | Lenovo Group Limited | 1.11 | 7827 | 61EEA3608B65D6750B4BE7838679C861 |
| 48 | C:\PROGRA~1\Lenovo\HOTKEY\tpnumlkd.exe | On screen display | Lenovo Group Limited | 1.21 | 13604 | 0D03C600686D80441AF87F9695312FBB |
| 49 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.35 | 16748 | 2B6A7F3D700545546C70D1DCD83BA464 |
| 50 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.77 | 19457 | C6D2404E3CCD5C3A6457E3E82D21709F |
| 51 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.40 | 18687 | 2BE2E4AD74B807691A3E8D2A6718BADB |
| 52 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.47 | 18687 | 241A4865C177B56B4A6ED0F306CC0F8A |
| 53 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.45 | 18687 | 9B125F72268189CFB955E76D88C3D449 |
| 54 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.77 | 19560 | F2801A1731637BC72FA8ACBABA80194A |
| 55 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.76 | 19457 | BA6E650E368521DF0820DE071FA130C7 |
| 56 | D:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.34.0 | 9425 | 9BB2ABA91D3F9A55DDDCF929703C7F0E |
| 57 | C:\PROGRA~1\Lenovo\HOTKEY\tpnumlkd.exe | On screen display | Lenovo Group Limited | 1.22 | 13552 | 4B65B2918E301026CC4D40A9E47290B0 |
| 58 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.50 | 18692 | 1765C22E1C77FE5AC591B8719FA3AB13 |
| 59 | D:\PROGRA~1\Lenovo\HOTKEY\tpnumlkd.exe | On screen display | Lenovo Group Limited | 1.22 | 13552 | 4B65B2918E301026CC4D40A9E47290B0 |
| 60 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.78 | 19565 | 6812D4B7E2B70E0CFB7BD78A56674EE9 |
| 61 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.79 | 19464 | ECE54F316433572B0212890EBFBC7801 |
| 62 | C:\PROGRA~1\Lenovo\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.31 | 13655 | 9A0DC212841D6062890CB2B445281121 |
| 63 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.79 | 19565 | FFB313E23187095D81D1BB245EAD3131 |
| 64 | C:\PROGRA~1\Lenovo\HOTKEY\tpnumlkd.exe | Unknown | 7827 | |||
| 65 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.52 | 18641 | C8A5EC440C16939EBC8CE4E1030EA5AF |
| 66 | C:\PROGRA~1\Lenovo\HOTKEY\tpnumlkd.exe | On screen display | Lenovo Group Limited | 1.11 | 7827 | 6666765ACF1B3A03230378514FFD9477 |
| 67 | C:\PROGRA~1\Lenovo\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.30 | 13655 | 8445529412EB0F9A9BB172C052B78171 |
| 68 | C:\PROGRA~1\Lenovo\HOTKEY\tpnumlkd.exe | On screen display | Lenovo Group Limited | 1.20 | 13552 | 85BC543102F30D55D4C5D6F8B9199335 |
| 69 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.79 | 19464 | ECE54F316433572B0212890EBFBC7801 |
| 70 | C:\PROGRA~2\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.34.0 | 9425 | 9BB2ABA91D3F9A55DDDCF929703C7F0E |
| 71 | D:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.79 | 19464 | ECE54F316433572B0212890EBFBC7801 |
| 72 | C:\ARCHIV~1\Lenovo\HOTKEY\tpnumlkd.exe | On screen display | Lenovo Group Limited | 1.21 | 13604 | 0D03C600686D80441AF87F9695312FBB |
| 73 | C:\Windows\System32\DriverStore\FileRepository\FN0CFB~1.INF\driver\TPNUMLKD.EXE | On Screen Display | Lenovo Group Limited | 2.21 | 459664 | 433E4AFC05A5F577A0A7A097D52A0571 |
| 74 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.79 | 215120 | D9F101B1E62B43535DF029D8AE8163CE |
| 75 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.34.0 | 106544 | 7FBDD37CEF8273CBD08D4C3A6FD84DCE |
| 76 | C:\WINDOWS\System32\DriverStore\FileRepository\fn.inf_amd64_62cf4e1fc023f9a9\driver\TPNUMLKD.EXE | On Screen Display | Lenovo Group Limited | 2.21 | 459664 | 433E4AFC05A5F577A0A7A097D52A0571 |
| 77 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.79 | 216136 | E86015F048E405B32463BFE22F28818E |
| 78 | C:\Windows\System32\DriverStore\FileRepository\FN531F~1.INF\driver\TPNUMLKD.EXE | On Screen Display | Lenovo Group Limited | 2.21 | 459448 | 7AEB85B9CB187E969BD16070FC6A58CE |
| 79 | C:\PROGRA~1\Lenovo\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.32 | 148032 | 7D8D43682A25A69F38F13D11AE0DD07B |
| 80 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.72 | 210376 | 882CD3F832AA412A83100ACBBAA0B5AD |
| 81 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.79 | 215120 | D9F101B1E62B43535DF029D8AE8163CE |
| 82 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.74 | 210328 | 0582C7915A7E84E385F34727656EAA9E |
| 83 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.53 | 237616 | B1792BAC62AB3262C26204C500140F1A |
| 84 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.45 | 207352 | 7A113E263A4540B2975BD3AF02B5E2C2 |
| 85 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.75 | 209064 | 05E5C656CE924F1DC65D5A1DBE5D8BE0 |
| 86 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.33.1 | 107664 | A470093B8E24AA4993F842EC7595BEC3 |
| 87 | C:\WINDOWS\System32\DriverStore\FileRepository\FN187F~1.INF\driver\TPNUMLKD.EXE | On Screen Display | Lenovo Group Limited | 2.21 | 495944 | D47B757FEEB8BB1D8E07DBB3AF0EFD4C |
| 88 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.45 | 207352 | 7A113E263A4540B2975BD3AF02B5E2C2 |
| 89 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.51 | 207408 | 8C6F2882D2EBB71119290E863D123ACB |
| 90 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.71 | 208328 | B74BAAC16532256C40145FF8D092E398 |
| 91 | C:\WINDOWS\System32\DriverStore\FileRepository\FN9A3B~1.INF\driver\TPNUMLKD.EXE | On Screen Display | Lenovo Group Limited | 2.21 | 459664 | 3A8E94D8B27A960A37498B7DD43F7D15 |
| 92 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.55 | 267720 | 2A296E553094A602CC3D05BD1F8417B0 |
| 93 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.34.0 | 106544 | 7FBDD37CEF8273CBD08D4C3A6FD84DCE |
| 94 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.53 | 237616 | ACBB6A2954336DAF27D354E57AFC575B |
| 95 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.46 | 207352 | 11EDC531ECC8BDBF39C4EF137AEC7197 |
| 96 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.35 | 182848 | 0AEA548F41CD36386BAE25963225BD87 |
| 97 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.55 | 267720 | F2200F5B9C79C6C16CF14E5C05184674 |
| 98 | C:\PROGRA~1\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.50 | 207408 | 0C7E0A4F15CCCF67DCDE1646C859746E |
| 99 | C:\Program Files\LENOVO\HOTKEY\tpnumlkd.exe | On Screen Display | Lenovo Group Limited | 1.40 | 207352 | FBBEDD48941C33470CB8BFE07F5C43FA |
| 100 | C:\PROGRA~1\Lenovo\HOTKEY\tpnumlkd.exe | On screen display | Lenovo Group Limited | 1.22 | 144232 | 66D5C5D140A1DBA3ECB1BFC155CF2074 |
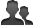 Comments about this process:
Comments about this process:
-------------------------------------------------------------------------------------------------------------------------------------------------------------By john 2024-05-31 17:41:38 Obtaining user operating system (OS) credentials from a targeted device is among threat actors’ primary goals when launching attacks because these credentials serve as a gateway to various objectives they can achieve in their target organization’s environment, such as lateral movement. One technique attackers use is targeting credentials in the Windows Local Security Authority Subsystem Service (LSASS) process memory because it can store not only a current user’s OS credentials but also a domain admin’s.
LSASS credential dumping was first observed in the tactics, techniques, and procedures (TTPs) of several sophisticated threat activity groups—including actors that Microsoft tracks as HAFNIUM and GALLIUM— and has become prevalent even in the cybercrime space, especially with the rise of the ransomware as a service gig economy. Detecting and stopping OS credential theft is therefore important because it can spell the difference between compromising or encrypting one device versus an entire network. Security solutions must provide specific measures and capabilities to help harden the LSASS process—for example, Microsoft Defender for Endpoint has advanced detections and a dedicated attack surface reduction rule (ASR) to block credential stealing from LSASS.
In May 2022, Microsoft participated in an evaluation conducted by independent testing organization AV-Comparatives specifically on detecting and blocking the LSASS credential dumping technique. The test, which evaluated several endpoint protection platforms (EPP) and endpoint detection and response (EDR) vendors, is the first time AV-Comparatives focused on a single attack technique, and we’re happy to report that Defender for Endpoint passed all 15 test cases used to dump user OS credentials from the LSASS process, achieving 100% detection and prevention scores. Notably, we also passed all test cases with only Defender for Endpoint’s default settings configured, that is, with LSASS ASR and Protective Process Light (PPL) turned off to validate our antivirus protection durability in itself. Such results demonstrate our continued commitment to provide organizations with industry-leading defense.
In this blog, we share examples of various threat actors that we’ve recently observed using the LSASS credential dumping technique. We also provide details on the testing methodology done by AV-Comparatives, which they also shared in their blog and detailed report. Finally, we offer additional recommendations to further harden systems and prevent attackers from taking advantage of possible misconfigurations should they fail to leverage credential dumping.
LSASS credential dumping: What we see in the wild
Dumping LSASS credentials is important for attackers because if they successfully dump domain passwords, they can, for example, then use legitimate tools such as PsExec or Windows Management Instrumentation (WMI) to move laterally across the network. They can also use techniques like pass-the-hash for lateral movement if they manage to obtain the password hashes.
Microsoft researchers are constantly monitoring the threat landscape, including the different ways threat actors attempt to steal user credentials. The table below is a snapshot of the most popular credential theft techniques these actors used from March to August 2022 based on our threat data:
Living-off-the-land binary (LOLBin) or hacking tool Threat actor that frequently uses this (not exhaustive)
Comsvc.dll (and its “MiniDump” export) loaded by rundll32.exe DEV-0270 (now tracked as Storm-0270*)
Mimikatz (and its modified variants) DEV-0674 (now tracked as Seashell Blizzard*)
Procdump.exe (with -ma command line option) Multiple threat actors
Taskmgr.exe DEV-0300 (now tracked as Storm-0300*)
*In April 2023, Microsoft Threat Intelligence shifted to a new threat actor naming taxonomy aligned around the theme of weather. To learn about how the new taxonomy represents the origin, unique traits, and impact of threat actors, and to get a complete mapping of threat actor names, read this blog: Microsoft shifts to a new threat actor naming taxonomy.
The first column shows the technique attackers most frequently used in their attempt to dump credentials from LSASS, while the second column shows which threat actor uses this technique most frequently. Based on the incidents we tracked from March to August 2022, credential theft attacks using LOLBins such as comsvc.dll, procdump.exe, or taskmgr.exe are still popular. These LOLBins are legitimate, digitally signed binaries that are either already present on the target device or are downloaded onto the system for the attacker to misuse for malicious activities.
Microsoft Defender Antivirus prevents the execution of these command lines due to its synchronous command line-blocking capabilities.
AV-Comparatives test
To evaluate EPP and EDR capabilities against the LSASS credential dumping technique, AV-Comparatives ran 15 different test cases to dump credentials from the LSASS process using both publicly available hacking tools like Mimikatz (which the tester modified to bypass antivirus signatures) and privately developed ones. These test cases were as follows:
Test case LSASS attack method
01 Mimikatz with process herpaderping
02 Native APIs DLL
03 Silent process exit
04 Alternative API snapshot function
05 MalSecLogon
06 Dump LSASS
07 Duplicate dump
08 PowerShell Mimikatz
09 Invoke Mimikatz (PoshC2)
10 SafetyDump
11 RunPE snapshot (PoshC2)
12 Unhook (Metasploit framework)
13 Reflective DLL (Metasploit framework)
14 Invoke Mimikatz (PowerShell Empire)
15 Invoke-PPL dump (PowerShell Empire)
Each test case implemented a comprehensive approach on how to dump credentials from LSASS. After the evaluation, AV-Comparatives shared the logs and detailed description of the test cases. Microsoft participated using Defender for Endpoint, both its antivirus and EDR capabilities, with only the default settings configured.
During the initial run, Defender for Endpoint prevented 11 out of 15 test cases and alerted/detected three of the remaining ones (Figure 1). We then made improvements in our protection and detection capabilities and asked AV-Comparatives to re-test the missed test cases. During the re-test, we prevented all the remaining four test cases, achieving 15 out of 15 prevention score.
Table showing the AV-Comparatives test cases and the corresponding results for Microsoft Defender for Endpoint (rows) in the following areas (columns): LSASS dumping was possible, Extracting credentials (offline) from respective minidump file was possible, Prevention by AV module, and Detection by EDR module.
Figure 1. Table showing how Defender for Endpoint prevented/detected the test cases in the first run of the AV-Comparatives test. The antivirus module missed test cases 01, 03, 09, and 10. We added improvements to the product based on these findings, thus allowing Defender for Endpoint to achieve 100% prevention score on re-test. (Source: AV-Comparatives)
We’d like to thank AV-Comparatives for this thorough test, which led us to improve our protection and detection capabilities in Defender for Endpoint. These improvements have already been rolled out to benefit our customers, and we’re looking forward to the next similar test. We aim to provide industry-leading, cross-domain defense, so it’s important for us to participate in tests like AV-Comparatives and MITRE Engenuity ATT&CK Evaluations because they help us ensure that we’re delivering solutions that empower organizations to defend their environments.
Securing the LSASS process with coordinated threat defense and system hardening
The continuous evolution of the threat landscape has seen attacks leveraging OS credential theft, and threat actors will continue to find new ways to dump LSASS credentials in their attempts to evade detection. For Microsoft, our industry-leading defense capabilities in Microsoft Defender for Endpoint are able to detect such attempts. We’ve also introduced new security features in Windows 11 to harden the operating system, such as enabling PPL for the LSASS process and Credential Guard by default. However, evaluations like this AV-Comparatives test go hand in hand with threat monitoring and research because they provide security vendors additional insights and opportunities to continuously improve capabilities.
Our teams performed an in-house test of all these test cases with the LSASS ASR rule enabled to check the protection level of that rule. We’re happy to report that the ASR rule alone successfully prevented all the tested techniques. The LSASS ASR rule is a generic yet effective protection our customers can implement to stop currently known user-mode LSASS credential dumping attacks. Defender customers should therefore enable this ASR rule—along with tamper protection—as an added protection layer for the LSASS process.
On top of the various dumping techniques, we’ve also observed threat actors attempt to weaken the device settings in case they can’t dump credentials. For example, they attempt to enable “UseLogonCredential” in WDigest registry, which enables plaintext passwords in memory. Microsoft Defender Antivirus detects such techniques, too, as Behavior:Win32/WDigestNegMod.B.
Windows administrators can also perform the following to further harden the LSASS process on their devices:
Enable PPL for LSASS process; note that for new, enterprise-joined Windows 11 installs (22H2 update), this is already enabled by default
Enable Windows Defender Credential Guard; this is also now enabled by default for organizations using the Enterprise edition of Windows 11
Enable restricted admin mode for Remote Desktop Protocol (RDP)
Disable “UseLogonCredential” in WDigest
Finally, customers with Azure Active Directory (Azure AD) can follow our recommendations on hardening environments:
Ransomware as a service: Understanding the cybercrime gig economy and how to protect yourself – Microsoft Security Blog
Best Practices for Securing Active Directory | Microsoft Learn
Pass the Hash | Microsoft Learn